Anonymous submission to MTL Counter-info
Here is a zine detailing how anti-extractivists can disrupt coal rail infrastructure utilising the tactic of unloading coal trains. Each page has been uploaded as an image.

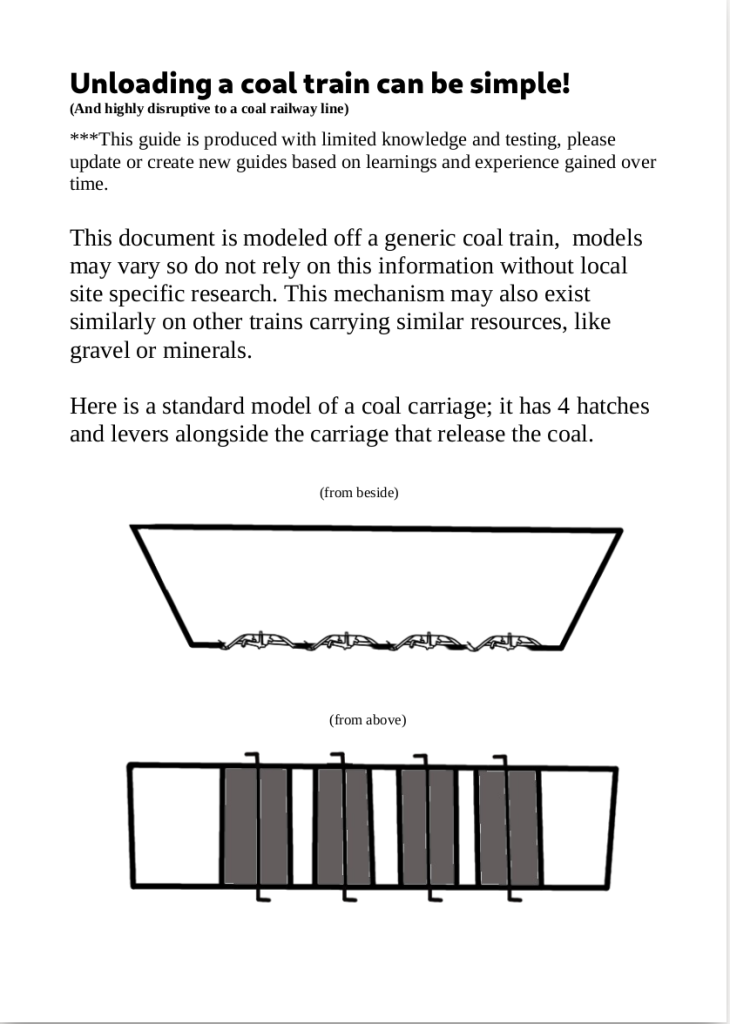
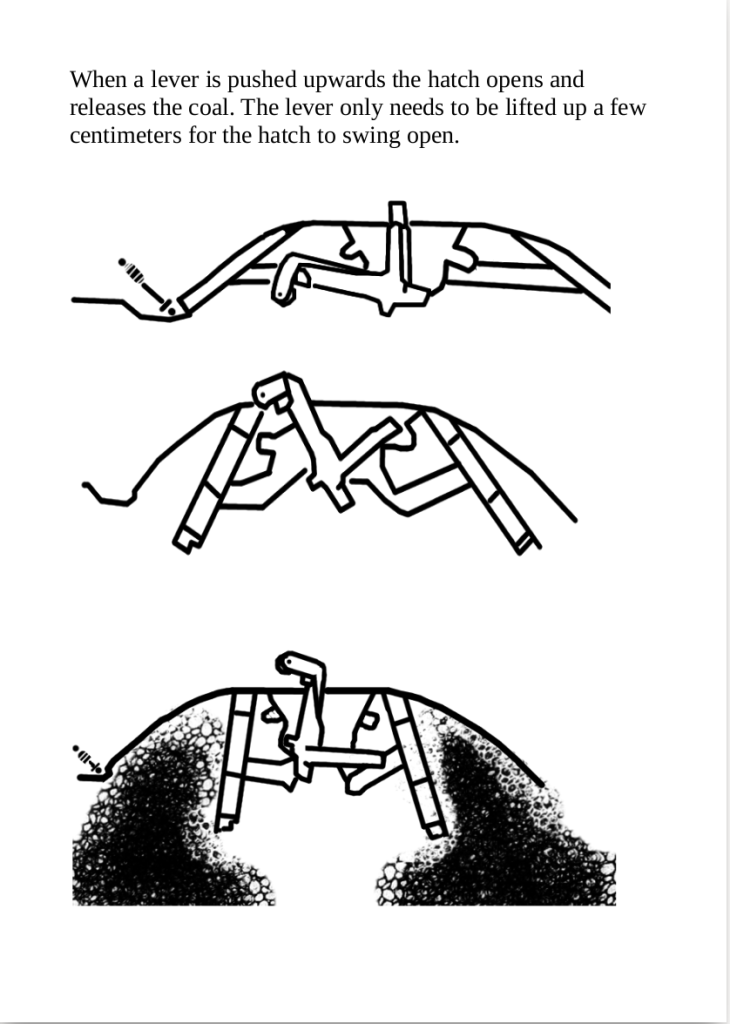

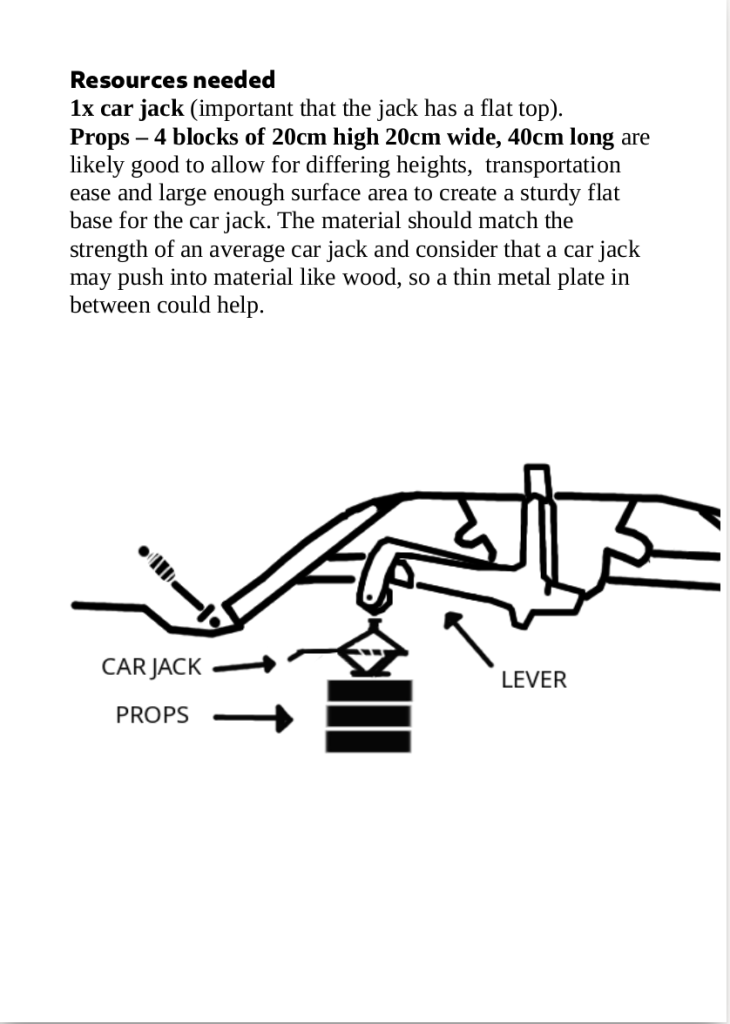




From No Trace Project
A communiqué, also sometimes called a reportback or hit report, is a report on (typically) illegal direct actions that is shared online via counter-info sites or in print publications. Mainstream media may suppress reporting about certain tactics or the reason for choosing a target may be unclear, so submitting a communiqué is a way to share news, tactics, and political motivations directly.This guide describes how to securely submit an anonymous communiqué online. It is written for anarchists, but could be useful to other audiences like journalists or dissident groups sharing information while concealing their identities. While some communiqués are signed by a group or individual claiming responsibility, this guide focuses on anonymity.
Nothing you do on computers or the internet is ever totally safe, but you can reduce most technology-based risk by following some simple steps. There are many methods beyond those shared here, but this is a set of instructions that will hopefully help you.
Communiqué: A report on (typically) illegal direct actions that is shared online via counter-info sites or in print publications.
Threat model: An analysis of risks that could compromise security, how likely they are to happen, and how they may be mitigated.
Tor: Short for “the onion router.” Tor is a strong anonymity system that routes your internet traffic through a series of random volunteer-run nodes across the planet. Learn more and download Tor Browser at torproject.org.
Browser: The application that allows you to access the internet. In addition to Tor Browser, other common examples include Firefox, Edge, Brave, and Chrome.
Operating system: Software programs that tell the hardware in a computer how to function. Common examples include Windows, Mac, Linux, and Tails.
Tails: An operating system that runs off a flash drive and leaves very few digital forensic traces on your computer. Tails also provides strong anonymity to your browsing traffic by routing all of it through Tor. Learn more and install at tails.net.
Stylometric analysis (stylometry): A forensics technique that analyzes word choice and style to identify authors and guess about their characteristics, for example regional dialect, education level, and unique word choice/phrases/typos.
Metadata: Data about data. For digital media, this is data contained within a photo or video file like camera type and date and time of capture. It can also refer to data about your typical patterns of internet use or date and time an account is created.
Disposable email: An anonymous email account that is temporary or single-use, typically with no login or account information. Also sometimes marketed as “spam email” sites.
Encryption: A method of hiding content in a message so it is only visible to your intended recipient.
Make or borrow a Tails stick, a USB drive that contains files to run the amnesiac operating system Tails. Install from tails.net or ask a tech-savvy friend to help you with the process. When making your Tails stick, use Tor Browser and space it out from when you send the actual communiqué so as to not leave as strong of a correlation. Making your own Tails stick is recommended over borrowing one since that keeps your digital habits or plans more private and makes it harder to compromise multiple people’s security through one contaminated device.
The general recommendation for most people is to use a personal computer that is only for Tails, on public WiFi. The risks of using Tails on a personal computer that you also use for other tasks are fairly low, but not zero. Avoid sitting where your screen or keyboard would be visible to any surveillance cameras. (If you are fast enough at it, single stall public restrooms or restrooms with tightly closing stalls can be great for this.)
Depending on your threat model, different computer and network options could be better suited to your security needs. Using public WiFi or a public computer (for example in a library or cybercafé) could reveal information about your movements, especially if you are already under physical surveillance. Public computers themselves could be compromised at the hardware level or through intentional collaboration between their owner-operators and law enforcement, and this could be almost impossible to detect. Using a device in your home, on your home WiFi, could leave you more vulnerable to threats like hidden cameras or sophisticated Tor correlation attacks. And, of course, if the place where you store your computer is insecure, the device could be compromised by hardware tampering (like a keylogger) or malicious software (less likely to matter when using Tails). For more information on threat modeling for your specific situation and learning about ways these attacks have been used against other activists, visit the No Trace Project (notrace.how) or AnarSec (anarsec.guide).
Plug the Tails stick into the computer while it is off. Turn on the computer and hold down specific keys to access the boot menu. Refer to the included table (taken from tails.net, which also has more detailed instructions) to see which keys are relevant for your device. If you must search for this information online, use Tor Browser and try to space that search out significantly from when you intend to submit your communiqué.
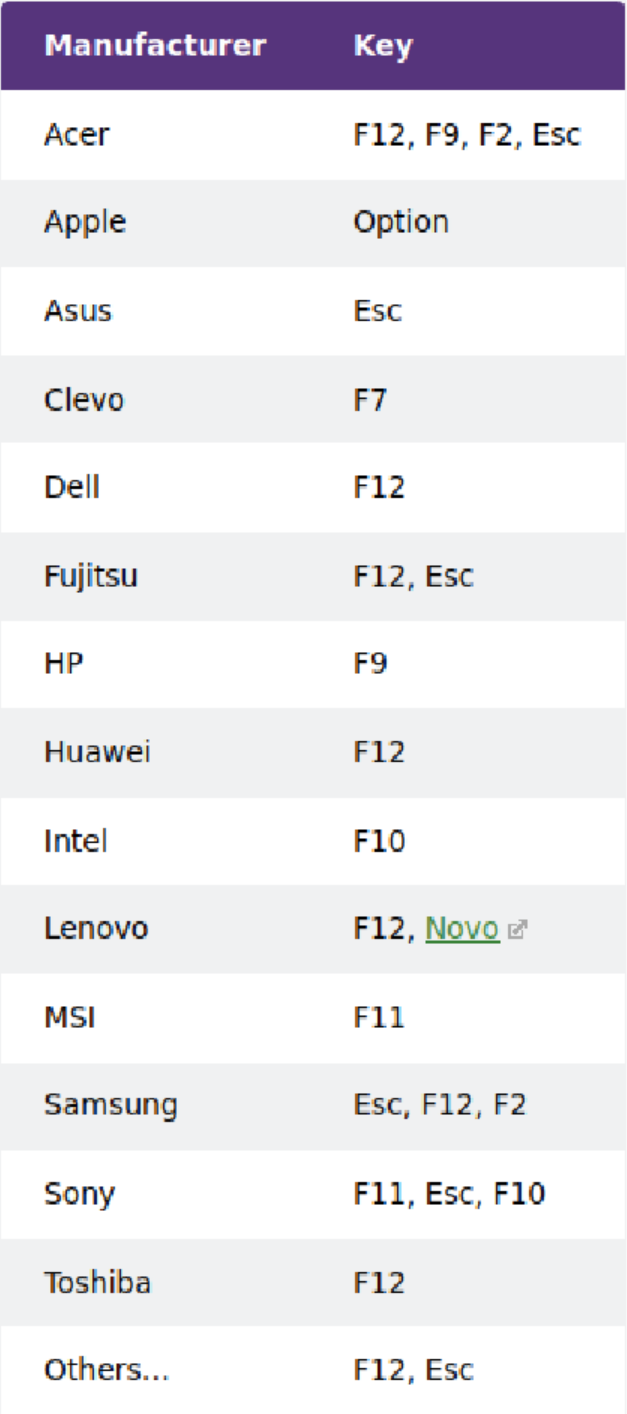
On startup, you will probably see phrases like “Press [key] to access boot menu” or “Press [key] to access BIOS options”. Some computers tell you to “Press [key] to interrupt normal startup” which brings you to the boot menu. From there, select your USB drive from the list and your computer will boot into Tails.
At the Tails welcome menu, when given the option to unlock Persistent Storage (if you have it set up), do not. Anything saved to Persistent Storage will be impossible to truly delete, short of reformatting and destroying your Tails stick. If you must save data between Tails sessions, use a second encrypted USB that you can destroy afterwards. To learn how to create an encrypted USB on Tails, read “Tails for Anarchists” on anarsec.guide.
Tails comes with many helpful programs pre-installed, including Tor Browser (to access the internet), Metadata Cleaner (to remove metadata from files including photos & videos), GIMP (for photo editing), the LibreOffice Suite (open-source versions of Microsoft Word/PowerPoint/Excel), and more.
Connect to the internet and use Tor Browser to identify counter-info sites that may be interested in your communiqué. Here are some relevant sites, sorted by region:
North America:
Europe:
Central & South America:
International:
These sites usually have a “contact” or “submissions” page which tells you how to send information you want published. This can be an email address or a form built into the website. Some offer both options (see steps 5-7).
(If your action has already been reported in the mainstream media, consider whether publishing a communiqué is worth the risk. Ask yourself: Does it include specific helpful information that will encourage other people to act? Will your intended audience see the already existing reporting? Does the target of the action understand why it happened, if that is important? Sometimes it may be better to submit a mainstream news article to counter-info sites, instead of writing an original communiqué.)
If you decide that writing your own submission is worthwhile, type your communiqué in a text editing program like LibreOffice Writer or Text Editor, NOT in the browser. The timing of keystrokes is very unique, especially for large blocks of text, and tracked by default on many web services. Do not save the document.
Only include information the police already know. Don’t add details like how many of you were involved, your background or identities, where you got supplies, entry or escape routes, or a long and stylistically unique personal political diatribe. These could unintentionally help an investigation against you.
To avoid stylometric analysis identifying you or grouping multiple of your submissions together, keep it short — less than 300 words if you can. If you’re writing with a friend, edit collaboratively to disguise your style. LibreOffice Writer can check for typos and punctuation errors, but will usually try to enforce formal linguistic rules. Unusual or specific dialect choices could help investigators link a communiqué to other writing. Making all letters the same case (upper or lowercase) disguises some style choices, but can be notable as a style choice itself. Some people recommend running text through Google translate or similar software to further disguise specific word choices and phrasing. This can be especially effective when translating between several languages with less online prevalence and/or different translation engines between languages. An English translation of the text “Who wrote that?” from Zündlumpen #76 deals with this topic extensively.
First, seriously consider if posting visual media of your clandestine action, especially videos, is worth it. Such media can give investigators a lot of information they might not have already have. Read up on open source intelligence techniques and video analysis. Details like faces, skin, tattoos, scars, height, gait, or unique clothing or accessories could lead to identification. For videos, things as simple as the hum of the electrical wires in your walls, road noise, or a single leaf can give very damaging information to the police, or any bored person with a laptop and an internet connection (yes really, any). And of course, the sound of your voice or car engine could be damning. Best practice is to use a burner camera (obtained for this purpose only, then discarded) to avoid photos or videos from different actions being linked together based on sensor noise.
If you decide submitting photos or videos is worth the risk, compress them to remove extra details by reducing the number of pixels. Lower resolution media can support your overall message without accidentally providing evidence like detailed reflections or tread marks. As a bonus, this reduces the file size which will make it easier to upload and share. For images, open them in GIMP then go to “File > Export As”. Click “Select File Type” and choose “JPEG” from the list. Use the “Quality” slider to reduce image quality, using the preview to check that it isn’t degraded too much.
Compressing videos is more complicated; look at the Tails OS documentation on sound and video for suggested programs and how to install them. There are websites that compress videos for you, but the most secure option is always something offline. If you upload a high-quality version to any website, that website could retain a copy and/or provide information to law enforcement. If you are in doubt about the potential evidence contained in your video, or are unsure how to remove potentially-identifying information, it might be best to leave it out of your submission entirely.
Once your files are compressed, the final step is to remove metadata, digital information that isn’t visible in the media but can be viewed in the file properties. Open Metadata Cleaner, click the “Add files” icon in the top left, and select your files. Click “Clean” in the bottom right to remove metadata and overwrite the originals.
As mentioned in step 3, some counter-info sites have built-in submission forms. These are often an easy and secure option to submit a communiqué, especially if you are sending only text. Each site is slightly different, so check the “submissions” or “contact” page for the exact sites where you want to send your communiqué.
Some sites accept media files through their online form, while others suggest specific filesharing sites. If files cannot be uploaded directly, one option is to upload them to file.espiv.net so you can paste a URL into a text box instead of attaching a media file directly to your submission. Note that some counter-info sites may not accept files submitted this way, as it poses a risk to site administrators. Check the relevant submission guidelines and use their suggested file sharing site(s) if available.
Paste your communiqué into the text field, enter fake non-identifying information in any other fields, upload cleaned media files or paste the filesharing URL if applicable, and submit! If that all works, skip to step 9.
If the site you want to submit to just has an email address or you experience technical difficulties using their submission form (including the communiqué not being received, which you might not notice until days later if it hasn’t been posted yet), it may be better to send your communiqué via email, as detailed in steps 7-8.
If you are not using an in-site submission form, you can send an email from an account created just for this purpose. One option is Protonmail (proton.me) — many submission sites also use Protonmail, making your email end-to-end encrypted by default. Note that this encryption is not as strong as something like PGP through a trusted email provider and Protonmail as a company is not your ally (they previously collaborated with cops and lied about it). However, the contents of your message are intended to be posted publicly. The intent here is not to keep the contents of your message absolutely secret, but to minimize any metadata or personal identifying information you could accidentally send with your message. NEVER send identifying information in connection with a communiqué.
For the username, pick 2-3 random words. The website randomwordgenerator.com can help with randomness. Use a different set of random words for the password (ideally 6+ for good password security). Do not save this login information anywhere.
When using Tor, Protonmail will ask for a secondary method of verification. Enter a disposable email address created on guerrillamail.com, yopmail.com, tempr.email, or a similar disposable email site so you can receive the confirmation code.
If you do not want to use Protonmail, you could try sending your communiqué from a disposable email site. However, many of these sites only receive emails and the ones that let you send an email (tempr.email) are sometimes less reliable, especially with media attachments.
Consider trying multiple methods, or varying methods between communiqués, in order to avoid creating metadata about your submission process.
Paste your communiqué into the body of the email. If sending your email between two Protonmail accounts (or another service that advertises end-to-end encryption between accounts they provide), the content of your email will be encrypted. The subject line, however, is never encrypted — for the safety of you and your recipient put something vague in that field or leave it blank.
Photos can usually be attached directly to the email. Videos or other large files can be uploaded to Proton Drive (same account as the email) or file.espiv.net and sent as a link. Note that some counter-info sites may not accept files submitted this way, as it poses a risk to site administrators. Check the relevant submission guidelines and use their suggested file sharing site(s) if available.
Read over everything one last time to make sure there are no mistakes and you attached everything you wanted. Then send the email!
Close any open programs, do not save any login info, and do not use the email account (if you made one) for anything else. Shut down the computer and remove your Tails stick. It can be safely used again, with no connection to the prior session, on the same computer or a different one.
If relevant, delete any photos or videos then destroy and dispose of any camera or SD card used in the action. Breaking a device into small pieces is best (the NSA recommends pieces < 2 mm), which can be achieved in a good quality household blender. Other options include using a hammer, plumbing torch, or strong acid. Avoid inhaling fumes from burning, melting, or other chemical reactions with metals or plastics.
Consider disposing of this zine if you’re using a hard copy, by destroying it or gifting to a trusted friend. It doesn’t prove you’ve done any crimes, but wouldn’t look great in court as potential corroborating evidence.
That’s it! This might seem like a lot of steps at first, but it’s not that hard and gets easier every time you do it.
Stay safe, be dangerous, don’t get caught.
Relevant websites:
Анонімне надходження в MTL Counter-info
Note to readers: MTL Counter-info now accepts translations of how-to articles in additional languages. If you would like to translate an article from our how-to section, please get in touch or make an anonymous submission.
Дисклеймер: це відео призначене виключно для інформаційних цілей і жодним чином не заохочує й не виправдовує жодну незаконну діяльність.
Ми вважаємо, що важливо поширювати тактичні знання зі спротиву для майбутніх штормів повстання. Тактика спротиву може убезпечити нас, тому що поліція починає боятися. Нам потрібно бути обережними, граючи з вогнем, але з правильним підходом молотови можуть значно посилити нас на вулицях.
Інгредієнти:
Порожні пивні пляшки 500 мл
Рукавички
Бензин
Моторне масло
Лійка
Марля або смужки футболки
Скотч
Ніколи не торкайтеся матеріалів без рукавичок, щоб не залишити відбитки пальців.
Спочатку наполовину наповніть пивну пляшку сумішшю з 2/3 бензину і 1/3 моторного масла. Моторне масло продовжить і поширить горіння. Залиште вільний простір у пляшці, щоб вона заповнилась газом і коктейль вийшов більш вибухонебезпечним.
Для гніту (смужки тканини або марлі) зав’яжіть вузол, який пройде у шийку пляшки на 1 дюйм (2,54 см) від верху. Гніт повинен сягати бензину. Вузол повинен триматися, якщо перевернути пляшку догори дном. Використовуйте скотч, щоб зробити отвір більш герметичним, оскільки бензин випаровується.
Для більших молотових використовуйте пляшки з-під вина з кришкою, яку можна закрутити назад. Також підходять скляні пляшки з-під води з кришкою, яка закручується.
Молотови з пивних пляшок можна транспортувати в упаковці. Зав’яжіть їх у пакети для сміття, щоб зменшити запах бензину та не залишати відбитки пальців.
Перші 30 секунд після запалення найбезпечніші, для того щоб кидати молотов.
Для більших молотових можна використовувати пляшки з-під вина з кришкою, яка закручується назад. Пляшка з-під води також підходить.
Молотови з пивних пляшок можна транспортувати в упаковці. Зав’яжіть їх у пакети для сміття, щоб менше пахло бензином та щоб не залишати відбитків пальців.
Найбезпечніше кидати молотов не більше ніж через 30 секунд, після запалення.
Будьте в безпеці! Будьте злі!

From Seeds of Resistance
This guide is an improved version of the practical section of the To Settlers, By Settlers callout that we recently re-published. Thank you to the reader who brought it to our attention.
The aim of information here is to disrupt rail flow, not be a catalyst for derailment or accidents, which could further injure life or land.
As always, we encourage folks to think about your heart, as well as the longevity of these actions and overall struggle; a gentle reminder that you are being careful with yourselves, fingerprints and DNA – for everyone’s safety – and that repression often follows action.
Prints
Fingerprints can be removed from hard surfaces with isopropyl alcohol. Wipe each item thoroughly in case something gets accidentally left behind or discovered – but aim to leave nothing behind. Where possible, it could be useful to have one person’s sole role be to ensure the tracking and removal of all equipment and debris. Store and pack equipment in a brand new, clean bag and only remove if wearing gloves. Some individuals wear two sets of gloves to ensure the outer set have no chance of print residue, while others wash using isoprpyl.
DNA
DNA can be transferred in a number of ways. Ensure you’re being diligent; don’t touch your face and cough you’re your hands while wearing gloves. You should be masked anyway, but consider wearing a medical mask to reduce droplet transmission. Keep your hair brushed (to remove loose hair) and tied back tightly – even covered. Don’t smoke or spit or drop garbage anywhere near your target area on the day of, or during scouting. Don’t leave anything behind. Be careful not to injure yourself on fencing or sharp corners. Properly dispose of masks, hats, gear, or clothing by burning thoroughly away from the site. Rainy days can be messy but good; they help wash away, displace and contaminate all evidence, including fibre and DNA. While you can use fire to dispose of clothing or evidence after-the-fact, you shouldn’t count on any incendiary materials left on site being burned so completely that DNA can’t be obtained. In other words – don’t use an old rag or t-shirt that’s been kicking around your place to ignite a fire assuming it will be burnt and therefor not leave DNA evidence. You never know if the fire will finish burning the material. Several people have been caught making that error. Sodium hydroxide (aka lye) can be found in some drain cleaners or being used by soap making will dissolve cellular proteins and destroy DNA evidence. The best defense however is to avoid contamination at all with appropriate preparation.
A Note on Bleach: Commercial bleach can destroy DNA enough to keep it from being replicated and tested in a lab for analysis, but it’s most reliable on hard surfaces and not always a sure thing. It does not keep hemoglobin from being detected. Oxidized bleach (such as bleach with hydrogen peroxide) can keep hemoglobin from being detected and therefor tested, but also does not reliably destroy DNA within an appropriate timeline.
Bottomline: If you’re not sure, be sure.
Copper Wire Method
– DO NOT ATTEMPT THIS ON SUBWAY TRANSIT LINES; they carry electricity.
– You can use this method when engaging in group NVCD to immediately send a signal to stop all train traffic.
The steel rails of tracks act as part of a track circuit for something called “automatic block signalling” (ABS). A very low voltage is sent through the rails to track sensors to create a loop in sets of geographic blocks. When a train moves along them, the train axle disrupts or shortens the circuit and sensors pick that up to indicate the block is occupied, automatically closing traffic in that area to other trains.
You can replicate the tripping of the circuit sensors by attaching copper wire to opposing rails.
1) Use a higher gauge copper wire for maximum conductivity and wrap it around one rail and across to the other. You can attach to the rails by digging out some rock near a wooden railway tie, or bolts on the tracks if you use a wire brush to take off the rust. Jumper cables work as a quick action – just make sure they’re long enough, but they’re also more expensive than a roll of copper wire.

2) Wire two opposing fishplates together. Fishplates are a flat panel of steel bolted onto the side of the rails where each rail section joins another. A fishplate has a plastic/rubber covered wire coming out of one side of the plate. You can strip or move some of this plastic and attach copper wire directly to that, and then attach the other end to the opposing rail, rail bolt, or other fishplate wire (for the best connection). The benefit of this method is that small gauge copper wire will conduct enough to trip the signal, and smaller wire is cheaper. The downside is that sometimes fishplates aren’t right across from each other – you’ll need to scout your location to make sure it’ll work.
TIPS: the copper needs to be touching areas on both rails that are NOT rusty/oxidized and still conducting. HIGH gage copper wire is necessary if your only points of connection are slightly rusty/oxidized. Have a lookout for trains and security patrols. Have a plan before you start wrapping or potentially triggering sensors. You may need a small tool to clear some crushed rock under the rail before wrapping the wire. Find a good spot, dig out both rails, and wrap one rail first. Remember as soon as you trip the circuit by connecting the wire to both rails the ABS will be tripped indicating something is wrong with the track. Get out as soon as you can. Burying the cable with crushed rock, snow or dirt will make it harder to find/spot within the block.
Destroying Signal Boxes
Signal boxes are part of rail circuits. If you walk railways, you’ve probably seen them as large grey shed like structures, or small grey boxes affixed to poles. These boxes are the receptors and interpreters of ABS circuit signals, road arms, etc. The casings are metal and typically secured closed. The small boxes on posts have cables that emerge, trail to the ground and run to the tracks. Since these wires have electrical components we would advise against simply cutting them unless you have a fair handle on understanding electricity and grounding.
Another method to damage wires and electrical circuits is hot fire. This means more than just dousing the cords in a fuel and walking away (this burns hot but doesn’t last) – it means building and ensuring a hotter, longer lasting fire. One good way to extend the burn of fibre (cotton fabric or cotton balls) is to add petroleum jelly and work it in. You’ll be able to just light that, which acts as a wick. To increase the heat of a fire you can add rubber from bicycle inner tubes or tires. Getting a small established fire like this going either in the circuit box/house or where the cord enters the ground should take care of the circuits and do a fine job delaying rail traffic by activating the ABS system in a longer-lasting way.
Notes: Practice building this kind of fire to see what’s possible. Burning rubber creates toxic fumes. Remember that this is arson – authorities will investigate it more seriously than the copper wire method. Be careful: find a good spot, have lookouts and an entry/exit plan that doesn’t expose you to people, ensure you’re being careful with fingerprints & DNA, properly dispose of any equipment used, have EXCELLENT security culture & practices with your crew.
Destroying Steel Rails
How do you destroy steel rails that hold a lot of tonnage every day? The same way they put them together: welding.
If you don’t happen to have several hundred dollars worth of equipment and an oxy-acetylene torch setup, you can still effectively destroy steel with thermite.
Thermite is a fuel/oxidizer ratio that can be adjusted to burn hot enough to destroy car engine blocks. It’s not particularly dangerous to mix BUT it does burn very hot, and very brightly so take precautions. When properly prepared, this method requires very little on-site time: just place, light and walk away. It also provides maximum physical property damage as the rail or signal box will need complete replacement.
The simplest fuel to use is aluminum powder. This can be collected from older etch-a-sketches or manufactured with (real) aluminum foil in a coffee grinder or blender that you never want to use for it’s intended purpose again. It is also a component in some fireworks (usually the silver ones) and most exploding gun targets (the small foil package or grey dust you’re supposed to mix in). The finer the flakes/powder the easier the ignition and faster the burn. You’ll want a fairly fine powder.
Cautions: very fine aluminum dust is explosive. However, you’re unlike to be able to achieve it with a regular household blender. Just in case, don’t open the blender near any open ignition sources. Very fine aluminum powder is also hard to get out of clothing, equipment, countertops, off skin etc. Be prepared to spend some time doing clean up. Wear a mask to prevent inhalation.
The simplest oxidizer to use with aluminum powder is iron oxide – red iron rust. Again, you can collect chunks of this from old items and turn it into a fine powder, or easily manufacture it by soaking ‘0000 grain’ steel wool in a 1:1 mix of bleach and vinegar in an OUTSIDE area. Plain bleach will work as well. Let it sit for a day to create a paste, which can they be dried and used.
Cautions: mixing bleach and vinegar makes a gas you shouldn’t inhale. While this is the fastest way to produce rust, you need to be able to do it in an outside, ventilated area. Otherwise, go with a single liquid method and give it more time.
You will also need an ignition wick. It takes a hot burn to ignite metal fuel so a lighter won’t work, and a firework fuse likely won’t either. Use either a silver burning (indicative of magnesium component) fireworks sparkler, or a homemade wick of match heads rolled into aluminum foil. We’ve had most luck with the matches/tinfoil method.
Cautions: Sparklers may present some risk of early ignition if the sparks coming off them hit the thermite before anticipated.
Thermite Powder
Mix a ratio of 3 parts (in weight) iron oxide to 2 parts aluminum powder (in weight). Cut or puncture a small wick hole on the side of a container (i.e. tin can). Insert your wick a couple inches so that there will be contact with the mixture in the can, and then fill the container with powder. Place and light where needed.
TIPS: unless the powder mix is fine and compacted, the burn will be less efficient and produce less heat!
Hard/Cake Thermite
3 parts iron oxide (in weight), 2 parts aluminum powder (in weight), 2 parts plaster of paris (in weight).
Mix the powders together, mix with plaster of paris. Pour into mold (can, etc.), insert wick into cake a couple inches on an angle. Let dry and remove from mould.
Mouldable Thermite
8 parts aluminum powder (in weight), 3 parts iron oxide (in weight), 4 parts clay (in weight). Mix the powders well then add to clay. Insert wick a couple inches. Place where needed and light.
Final Cautions: Because the thermite method damages the rail itself, it presents a risk of derailment. To avoid this risk you may want to trip the ABS circuit by applying copper wire across the rails as well (method one). Again, this is a method police are likely to investigate thoroughly. Make sure all items you’re leaving behind are free of fingerprints and DNA. Have lookouts and careful off-camera approaches. Dispose of or destroy clothing and boots. Thermite burns hot and bright – do not stare after ignition. Very fine aluminum powder is reactive to oxygen and can ignite easily. If water (rain, snow, puddles) is added to burning thermite it will cause an explosion that sends molten iron flying outwards. DO NOT try to extinguish burning thermite with water.

Anonymous submission to North Shore Counter-Info
It’s important to know that settlers have written this. We don’t have the lived experience of any Indigenous person, including the Wet’suwet’en. We do write from a place of heart and affinity within this struggle – personal, political, and/or relational. In that we feel responsibility to act against the systems and corporations that harm the people and land within it. We acknowledge our settler responsibility and complicity in this, and look for opportunities and strategies that align politically as a way to enact solidarity. This does not mean we speak for them, or should be closed to critiques.
First, let’s address that for various reasons there has sometimes been a lack of clarity around what is being asked for by folks out west.
We want to gently remind friends reading this that some individuals have been restricted in providing any kind of direction or encouragement – or even speaking against the project. The gag is set by court orders which wield the threat of financial ruin and the loss of a ten year land-based healing project for an entire community. We remind ourselves that the people we may put into “leadership” positions may not want to be experiencing the pedestalization and fetishization of expectant settlers wanting firm answers – at great risk – on behalf of many.
Within and outside of this struggle, settlers are consistently directed to take responsibility for their fellow settlers and the ongoing processes and harms of colonization. As settlers hearing that, we are compelled to act in defiance of – and take an offensive position against – the state and industries that are willing to kill for profit, and pretend to be doing so in our interests.
We also want to acknowledge the lingering hopeless feeling that some of us felt when, after a decade of affirming a hard line, chiefs allowed for the Unist’ot’en gate to be opened. We know you know that compliance under threat of violence is not consent, but consideration exists even beyond that, like the RCMP delivering veiled and not-so-veiled threats to Chiefs at their homes in the middle of the nights. We encourage curiosity about whether hopelessness and disappointment went both ways here; to what extent did the low numbers of supporters who couldn’t or wouldn’t make it out after a decade of promise have impacts on positional outcome and aftermath? The writers of this personally take action when we feel at our strongest – rested, fed, grounded, encouraged, and supported. So what is our complicity – as settlers or allies or supporters who weren’t there or weren’t taking action from afar – in that gate opening?
Despite all of this the Wet’suwet’en never stopped asking for support and solidarity actions, and never stopped occupying their territories. And earlier today, the Wet’suwet’en and their supporters have again taken a physical stand to protect the Yintah, their way of life, and living for generations to come. They defend their very existence against the imperialist violence and colonialism of the Canadian state on behalf of private entities, and reject Canada and CGL’s authority and jurisdiction over their unceded lands.
We stand with them and are prepared to enact solidarity.
Further, we aim to inspire you to act friends & comrades!
Anarchists, comrades, radicals and likeminded folks in so-called Ontario have a longstanding history of solidarity actions with, for, and inspired by indigenous blockades and land projects. The enactments of support have been beautiful and courageous moments that have built lasting networks and relationships.
Dream big and help make it happen again!
The last year on the territory has seen large swaths of trees clear cut, wildlife displaced, a man camp established, artefacts and trap lines moved and destroyed, and the installment of an RCMP staffed “industry protection office” on unceded lands. The year also unveiled to all that the RCMP is prepared to kill Indigenous peoples to carry out the will of corporations.
Further, in a move that deliberately continues a legacy of genocide against all Indigenous peoples, justice Marguerite Church recently approved an interlocutory injunction against the Wet’suwet’en making it illegal for them under colonial law to defend their own lands against industry or Canada, as an invading Nation. Her decision states that “Indigenous law has no effectual place in Canadian law.” The injunction will allow for the destruction of Gidimt’en camp, cabins throughout the territory, and presents risk to the healing lodge.
Unsurprising and absolute imperialist bullshit.
Do you need more reasons? We didn’t think so.
Which leaves us with what we do.
As geographically distant allies the logical conclusion is that we will likely never get explicit, widespread permission or an “official” thumbs up (and we should certainly strive to understand our inclination to ask or want for those things), but with a few considerations we can get a fair sense of what’s needed, and wanted.
1) The intensity of the current situation. Today, Wet’suwet’en hereditary leadership have gathered to take a final stand and remove industry from their territory as a way to prevent further destruction of the land and water, ensuring their safety and livelihoods. Legal challenges have failed, and this is perhaps “it” – the final possibility of protecting their Yintah.
2) With this development will come new, increased and incensed calls for solidarity actions.
3) Actions that have received support or excitement previously include large militant disruptions such as highway and port blockades, occupations and attempted shutdowns of pipeline facilities, and the closure of a Shell terminal. No actions have yet been denounced.
4) Previous requests have included guidance to respect the agreements and responsibilities of the territory you are on, to respect the land, water, and life of it, and to honour and centre Indigenous messaging.
There is no shortage of existing opportunities, but thinking back to what we’ve seen work in this area, what is relevant, and what is strategic and what can embrace many tones and tactics, we think of rail disruptions.
Rail traffic creates excellent opportunity for state and economic disruption; infrastructure is so sprawling it’s relatively indefensible – particularly outside of cities. Geographical features create thousands of natural bottlenecks across Turtle Island which lend themselves as targets for maximum effectiveness using a broad range of methods. Historically even short disruptions – by actions or rail strikes – have had large economic impacts. After just two days of a recent rail strike the Federal government started drafting emergency legislation out of concern for the economy. In 2012, a 9 day disruption dropped the local GDP by 6.8%.
Imagine allies disrupting and damaging rail infrastructure and bottlenecks in Northern BC between Kitimat-Chetwynd-Houston-Stewart; it would orphan pipe stockpiles in ports, preventing their delivery to construction areas.
There is no need to chase the frontline; we can fight where we stand.
Rail sabotage works as both a tactic and a strategy, and so we’re calling for ongoing rail disruptions in solidarity with the Wet’suwet’en people who are currently defending their unceded territory from industry and police invasion.
Our suggestions include using copper wire to trip signal blocks, and the destruction of signal boxes and rail tracks – but even large public NVCD groups stopping essential rail lines is better than no action at all. Read on for details, safety tips, and links.
As always, we encourage folks to think about your heart, as well as the longevity of these actions and overall struggle; a gentle reminder that you are being careful with yourselves, fingerprints and DNA – for everyone’s safety – and that repression often follows action.
Prints
Fingerprints can be removed from hard surfaces with isopropyl alcohol. Wipe each item thoroughly in case something gets accidentally left behind or discovered. Store in a brand new, clean bag and only remove if wearing gloves.
DNA
DNA can be transferred in a number of ways. Ensure you’re being diligent; don’t touch your face and cough you’re your hands while wearing gloves. Keep your hair brushed (to remove loose hair) and tied back. Don’t smoke or spit anywhere near your target area. Don’t leave anything behind. Be careful not to injure yourself. Properly dispose of masks, hats, gear, or clothing (bleach, heat, or burn). Rainy days can be messy but good; they can help wash away, displace and contaminate fibre and DNA evidence. Bleach can destroy DNA by keeping it from being replicated in a lab for analysis. Heat and fire also destroy DNA well.
If you’re not sure, be sure.
Copper Wire Method
– DO NOT ATTEMPT THIS ON SUBWAY TRANSIT LINES; they carry electricity.
– You can use this method when engaging in group NVCD to immediately send a signal to stop all train traffic.
The steel rails of tracks act as part of a track circuit for something called “automatic block signalling” (ABS). A very low voltage is sent through the rails to track sensors to create a loop in sets of geographic blocks. When a train moves along them, the train axle disrupts or shortens the circuit and sensors pick that up to indicate the block is occupied, automatically closing traffic in that area to other trains.
By using a high gage (thick!) copper wire and wrapping it around and then across the rails one can replicate the tripping of the circuit sensors. Note: you don’t need to locate and connect the actual block sensors.
TIPS: the copper needs to be touching areas on both rails that are NOT rusty/oxidized and still conducting. HIGH gage copper wire is necessary. Have a lookout for trains and security patrols. Have a plan before you start wrapping. You may need a small tool to clear some crushed rock under the rail before wrapping the wire. Find a good spot, dig out both rails, and wrap one rail first. Remember as soon as you trip the circuit by connecting the wire to both rails the ABS will be tripped indicating something is up. Get out as soon as you can. Burying the cable with crushed rock, snow or dirt will make it harder to find/spot within the block.
Destroying Signal Boxes
Signal boxes are part of rail circuits. If you walk railways, you’ve probably seen them as large grey shed like structures, or small grey boxes affixed to poles. These boxes are the receptors and interpreters of ABS circuit signals. The casings are metal and typically secured closed somehow, and the small boxes on posts have cables that emerge, trail to the ground and run to the tracks. Since these wires have electrical components we would advise against simply cutting them unless you have a fair handle on electricity. Another method to damage wires and electrical circuits is hot fire. This means more than just dousing the cords in a fuel and walking away – it means building and ensuring a hotter, longer lasting fire. On good way to extend the burn of fibre tinder (cotton fabric or cotton balls are favourites with us) is to add petroleum jelly and work it in. You’ll be able to just light that, which acts as a wick. To increase the heat of a fire you can add rubber from bicycle inner tubes or tires. Getting a small established fire like this going either in the circuit box/house or where the cord enters the ground should take care of the circuits and do a fine job delaying rail traffic by activating the ABS system in a longer-lasting way.
Notes: Practise building this kind of fire to see what’s possible. Burning rubber creates toxic fumes. This is arson – which authorities will investigate more seriously than the copper wire method. Be careful: find a good spot, have lookouts and an entry/exit plan that doesn’t expose you to people, ensure you’re being careful with fingerprints & DNA, properly dispose of any equipment used, have EXCELLENT security culture & practises with your crew.
Destroying Steel Rails
How do you destroy steel rails that hold a lot of tonnage every day? The same way they put them together: thermite.
Thermite is a fuel/oxidizer ratio that can be adjusted to burn hot enough to destroy car engine blocks. It’s not particularly dangerous to mix BUT it does burn very hot, and very brightly so take precautions. This method requires very little on-site time: just place, light and walk away. It also provided maximum physical property damage as the rail or signal box will need complete replacement.
The simplest fuel to use is aluminum powder. This can be collected from older etch-a-sketches or manufactured with (real) aluminum foil in a coffee grinder. The finer the flakes/powder the faster the burn.
The simplest oxidizer to use with aluminum powder is iron oxide – red iron rust. Again, you can collect this and turn it into a fine powder, or easily manufacture it by soaking ‘0000 grain’ steel wool in bleach. Let it sit for a day to create a paste, which can then be dried and used.
You will also need an ignition wick. It takes a hot burn to ignite metal fuel so a lighter won’t work, and a firework fuse likely won’t either. Use either a common fireworks sparkler, or a homemade wick of match heads rolled into aluminum foil. Sparklers may present some risk of early ignition if the sparks coming off them hit the thermite before anticipated.
Thermite Powder
Mix a ratio of 3 parts iron oxide to 2 parts aluminum powder. Cut or puncture a small wick hole on the side of a container (i.e. tin can). Insert your wick a couple inches so that there will be contact with the mixture in the can, and then fill the container with powder. Place and light where needed.
TIPS: unless the powder mix is fine and compacted, the burn will be less efficient and produce less heat!
Hard/Cake Thermite
3 parts iron oxide, 2 parts aluminum powder, 2 parts plaster of paris. Mix the powders together, mix with plaster of paris. Pour into mold (can, etc.), insert wick into cake a couple inches on an angle. Let dry and remove from mould.
Mouldable Thermite
8 parts aluminum powder, 3 parts iron oxide, 4 parts clay. Mix the powders well then add to clay. Insert wick a couple inches. Place where needed and light.
Notes: Because this method damages the rail itself it presents a risk of derailment. To avoid this risk you may want to trip the ABS circuit by applying copper wire across the rails as well (method one). Again, this is a method police are likely to investigate thoroughly. Make sure all items you’re leaving behind are free of fingerprints and DNA. Have lookouts and careful off-camera approaches. Dispose of or destroy clothing and boots. Thermite burns hot and bright – do not stare after ignition. Very fine aluminum powder is reactive to oxygen and can ignite easily. If water (rain, snow, puddles) is added to burning thermite it will cause an explosion that sends molten iron flying outwards. DO NOT try to extinguish burning thermite with water.

From CrimethInc.
Turbulent times are upon us. Already, blockades, demonstrations, riots, and clashes are occuring regularly. It’s past time to be organizing for the upheavals that are on the way.
But getting organized doesn’t mean joining a pre-existing institution and taking orders. It shouldn’t mean forfeiting your agency and intelligence to become a cog in a machine. From an anarchist perspective, organizational structure should maximize both freedom and voluntary coordination at every level of scale, from the smallest group up to society as a whole.
You and your friends already constitute an affinity group, the essential building block of this model. An affinity group is a circle of friends who understand themselves as an autonomous political force. The idea is that people who already know and trust each other should work together to respond immediately, intelligently, and flexibly to emerging situations.
This leaderless format has proven effective for guerrilla activities of all kinds, as well as what the RAND Corporation calls “swarming” tactics in which many unpredictable autonomous groups overwhelm a centralized adversary. You should go to every demonstration in an affinity group, with a shared sense of your goals and capabilities. If you are in an affinity group that has experience taking action together, you will be much better prepared to deal with emergencies and make the most of unexpected opportunities.
This guide is adapted from an earlier version that appeared in our Recipes for Disaster: An Anarchist Cookbook.
Relative to their small size, affinity groups can achieve a disproportionately powerful impact. In contrast to traditional top-down structures, they are free to adapt to any situation, they need not pass their decisions through a complicated process of ratification, and all the participants can act and react instantly without waiting for orders—yet with a clear idea of what to expect from one another. The mutual admiration and inspiration on which they are founded make them very difficult to demoralize. In stark contrast to capitalist, fascist, and socialist structures, they function without any need of hierarchy or coercion. Participating in an affinity group can be fulfilling and fun as well as effective.
Most important of all, affinity groups are motivated by shared desire and loyalty, rather than profit, duty, or any other compensation or abstraction. Small wonder whole squads of riot police have been held at bay by affinity groups armed with only the tear gas canisters shot at them.
Some affinity groups are formal and immersive: the participants live together, sharing everything in common. But an affinity group need not be a permanent arrangement. It can serve as a structure of convenience, assembled from the pool of interested and trusted people for the duration of a given project.
A particular team can act together over and over as an affinity group, but the members can also break up into smaller affinity groups, participate in other affinity groups, or act outside the affinity group structure. Freedom to associate and organize as each person sees fit is a fundamental anarchist principle; this promotes redundancy, so no one person or group is essential to the functioning of the whole, and different groups can reconfigure as needed.

An affinity group can range from two to perhaps as many as fifteen individuals, depending on your goals. However, no group should be so numerous that an informal conversation about pressing matters is impossible. You can always split up into two or more groups if need be. In actions that require driving, the easiest system is often to have one affinity group to each vehicle.
Learn each other’s strengths and vulnerabilities and backgrounds, so you know what you can count on each other for. Discuss your analyses of each situation you are entering and what is worth accomplishing in it—identify where they match, where they are complentary, and where they differ, so you’ll be ready to make split-second decisions.
One way to develop political intimacy is to read and discuss texts together, but nothing beats on-the-ground experience. Start out slow so you don’t overextend. Once you’ve established a common language and healthy internal dynamics, you’re ready to identify the objectives you want to accomplish, prepare a plan, and go into action.
Affinity groups are resistant to infiltration because all members share history and intimacy with each other, and no one outside the group need be informed of their plans or activities.
Once assembled, an affinity group should establish a shared set of security practices and stick to them. In some cases, you can afford to be public and transparent about your activities. in other cases, whatever goes on within the group should never be spoken of outside it, even after all its activities are long completed. In some cases, no one except the participants in the group should know that it exists at all. You and your comrades can discuss and prepare for actions without acknowledging to outsiders that you constitute an affinity group. Remember, it is easier to pass from a high security protocol to a low one than vice versa.
Affinity groups generally operate on via consensus decision-making: decisions are made collectively according to the needs and desires of every individual involved. Democratic voting, in which the majority get their way and the minority must hold their tongues, is anathema to affinity groups—for if a group is to function smoothly and hold together under stress, every individual involved must be satisfied. Before any action, the members of a group should establish together what their personal and collective goals are, what risks they are comfortable taking, and what their expectations of each other are. These matters determined, they can formulate a plan.
Since action situations are always unpredictable and plans rarely come off as anticipated, it may help to employ a dual approach to preparing. On the one hand, you can make plans for different scenarios: If A happens, we’ll inform each other by X means and switch to plan B; if X means of communication is impossible, we’ll reconvene at site Z at Q o’clock. On the other hand, you can put structures in place that will be useful even if what happens is unlike any of the scenarios you imagined. This could mean preparing resources (such as banners, medical supplies, or offensive equipment), dividing up internal roles (for example, scouting, communications, medic, media liaison), establishing communication systems (such as burner phones or coded phrases that can be shouted out to convey information securely), preparing general strategies (for keeping sight of one another in confusing environments, for example), charting emergency escape routes, or readying legal support in case anyone is arrested.
After an action, a shrewd affinity group will meet (if necessary, in a secure location without any electronics) to discuss what went well, what could have gone better, and what comes next.

An affinity group answers to itself alone—this is one of its strengths. Affinity groups are not burdened by the procedural protocol of other organizations, the difficulties of reaching agreement with strangers, or the limitations of answering to a body not immediately involved in the action.
At the same time, just as the members of an affinity group strive for consensus with each other, each affinity group should strive for a similarly considerate relationship with other individuals and groups—or at least to complement others’ approaches, even if others do not recognize the value of this contribution. Ideally, most people should be glad of your affinity group’s participation or intervention in a situation, rather than resenting or fearing you. They should come to recognize the value of the affinity group model, and so to employ it themselves, after seeing it succeed and benefiting from that success.
An affinity group can work together with other affinity groups in what is sometimes called a cluster. The cluster formation enables a larger number of individuals to act with the same advantages a single affinity group has. If speed or security is called for, representatives of each group can meet ahead of time, rather than the entirety of all groups; if coordination is of the essence, the groups or representatives can arrange methods for communicating through the heat of the action. Over years of collaborating together, different affinity groups can come to know each other as well as they know themselves, becoming accordingly more comfortable and capable together.
When several clusters of affinity groups need to coordinate especially massive actions—before a big demonstration, for example—they can hold a spokescouncil meeting at which different affinity groups and clusters can inform one another (to whatever extent is wise) of their intentions. Spokescouncils rarely produce seamless unanimity, but they can apprise the participants of the various desires and perspectives that are at play. The independence and spontaneity that decentralization provides are usually our greatest advantages in combat with a better equipped adversary.
For affinity groups and larger structures based on consensus and cooperation to function, it is essential that everyone involved be able to rely on each other to come through on commitments. When a plan is agreed upon, each individual in a group and each group in a cluster should choose one or more critical aspects of the preparation and execution of the plan and offer to bottomline them. Bottomlining the supplying of a resource or the completion of a project means guaranteeing that it will be accomplished somehow, no matter what. If you’re operating the legal hotline for your group during a demonstration, you owe it to them to handle it even if you get sick; if your group promises to provide the banners for an action, make sure they’re ready, even if that means staying up all night the night before because the rest of your affinity group couldn’t show up. Over time, you’ll learn how to handle crises and who you can count on in them—just as others will learn how much they can count on you.
Stop wondering what’s going to happen, or why nothing’s happening. Get together with your friends and start deciding what will happen. Don’t go through life in passive spectator mode, waiting to be told what to do. Get in the habit of discussing what you want to see happen—and making those ideas reality.
Without a structure that encourages ideas to flow into action, without comrades with whom to brainstorm and barnstorm and build up momentum, you are likely to be paralyzed, cut off from much of your own potential; with them, your potential can be multiplied by ten, or ten thousand. “Never doubt that a small group of thoughtful, committed people can change the world,” Margaret Mead wrote: “it’s the only thing that ever has.” She was referring, whether she knew it or not, to affinity groups. If every individual in every action against the state and status quo participated as part of a tight-knit, dedicated affinity group, the revolution would be accomplished in a few short years.
An affinity group could be a sewing circle or a bicycle maintenance collective; it could come together for the purpose of providing a meal at an occupation or forcing a multinational corporation out of business through a carefully orchestrated program of sabotage. Affinity groups have planted and defended community gardens, built and occupied and burned down buildings, organized neighborhood childcare programs and wildcat strikes; individual affinity groups routinely initiate revolutions in the visual arts and popular music. Your favorite band was an affinity group. An affinity group invented the airplane. Another one maintains this website.
Let five people meet who are resolved to the lightning of action rather than the agony of survival—from that moment, despair ends and tactics begin.

Printable zine version of this article is also available for download.

Anonymous submission to MTL Counter-info
Recently, we went on a nighttime stroll and removed some Google Nest and Amazon Ring doorbell surveillance cameras from a couple residential streets.
These products, which one can easily spot at night by their blue or green ring of light, are popping up more and more in Montreal and elsewhere. The cameras can store recorded video on the cloud for up to 60 days.
It’s been well documented that Amazon is using Ring to build a private surveillance network, fully integrated with police departments, under the guise of combating package theft.
On a positive note, these doorbell cameras make it easy to fight back against the giants of techno-capitalism right in our neighborhoods. They are easily removed with a small crowbar. It’s suggested to have a buddy with you and/or wear electrical insulating gloves as a precaution against the risk of shock from live wires. And be aware that the battery-powered camera may continue recording and transmitting even after being torn from the wall, while it’s still in range of its home wifi network; the user may also receive a notification on their phone.
Fuck Amazon, Google, and their encroaching techno-dystopia.
 Anonymous submission to MTL Counter-info
Anonymous submission to MTL Counter-info
Over the past several days, motivated by an international call for transit fare strikes, the fare distribution machines in several metro stations were disabled by blocking the debit/credit card readers and coin slots.
The STM is continually hiking fares and deploying squads of wannabe-cop “inspectors” to harass, fine, and assault people over $3.50. Currently, the STM is even seeking to give its inspectors expanded powers to detain and arrest people and access police databases. Every effort to maintain and expand policing of people’s movements deserves to be met with resistance. Fortunately, there is no shortage of inspiration from around the world, above all the ongoing revolt in Chile.
These actions were experiments with some simple, effective, and fairly discreet means of sabotageing fare collection and enforcement. At this point in time, the method that gives us the most confidence is to apply super glue to both sides of a random unactivated gift card and insert it fully in the debit/credit card slot, and put more super glue in the coin slot after causing it to open by operating the machine as though you want to pay for a ticket with cash. We hope this technique can be reproduced widely alongside other tactics for taking these machines out of service.
Live free, ride free.
Anonymous Submission to MTL Counter-info
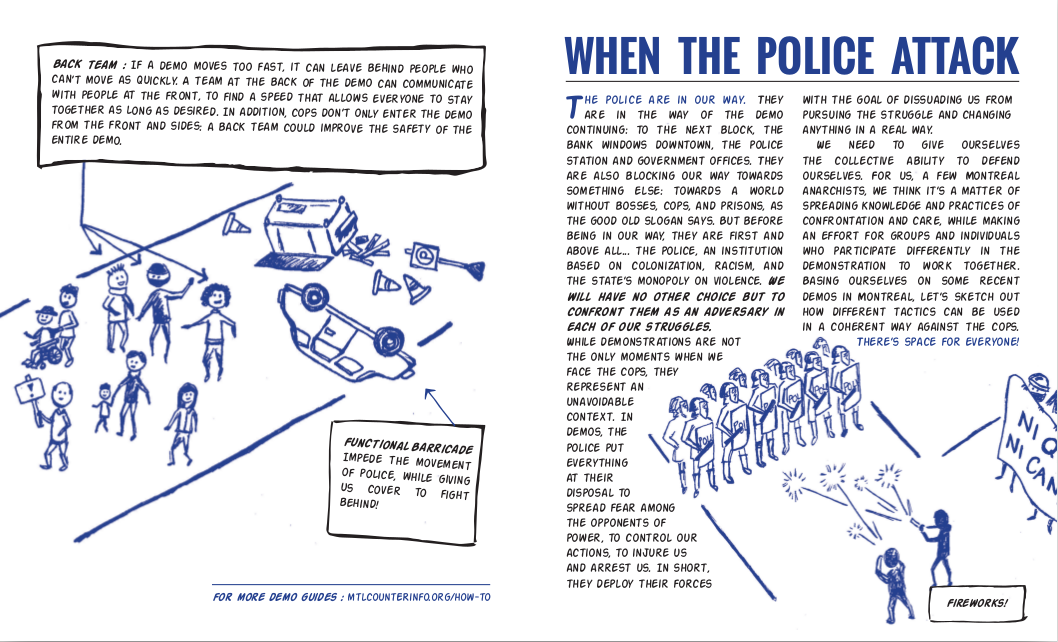
The police are in our way. They are in the way of the demo continuing: to the next block, the bank windows downtown, the police station and government offices. They are also blocking our way towards something else: towards a world without bosses, cops, and prisons, as the good old slogan says. But before being in our way, they are first and above all… the police, an institution based on colonization, racism, and the state’s monopoly on violence. We will have no other choice but to confront them as an adversary in each of our struggles.
While demonstrations are not the only moments when we face the cops, they represent an unavoidable context. In demos, the police put everything at their disposal to spread fear among the opponents of power, to control our actions, to injure us and arrest us. In short, they deploy their forces with the goal of dissuading us from pursuing the struggle and changing anything in a real way.
We need to give ourselves the collective ability to defend ourselves. For us, a few Montreal anarchists, we think it’s a matter of spreading knowledge and practices of confrontation and care, while making an effort for groups and individuals who participate differently in the demonstration to work together. Basing ourselves on some recent demos in Montreal, let’s sketch out how different tactics can be used in a coherent way against the cops. There’s space for everyone!

[PDF (en)]
[PDF (fr)]
Pipelines are war; one built from the insatiable greed of corporations which have normalized violence against the land and its living. Our resolve within this struggle intensifies with each audacious assault Enbridge launches; each time they dismiss the concerns and requests of Indigenous Nations. Every court proceeding. Every act of intimidation. Every lie or false claim of safety or necessity. We’ve had enough.
So back when Enbridge started shipping in pipeline segments for their line 10 expansion, we started sabotaging them.
There are vast networks of pipeline infrastructure throughout Turtle Island. They are indefensible; perfect opportunities for effective direct action that harms nothing but an oil company’s bottom line. It’s in this spirit that we found ourselves going for long moonlit strolls through the trenches of the freshly dug line10 right-of-way. Wherever we felt the urge, we drilled various sized holes into pipeline segments while spilling corrosives inside others.
We do this in solidarity with the Indigenous peoples of this area. A people who have been displaced, threatened and murdered since early colonial arrivals – who still continue to face this violence. Who suffer the consequences of this colonial capitalist society and the industries which drive it.
So – to Enbridge: You’re gonna want to replace every last section of line 10 that’s been laid out so far. We say this because we care for the environment, and don’t care about you – so take it seriously. And for every dollar you pursue from Indigenous Nations or individuals for defending their territories, we aim to cost you ten. #sorrynotsorry
To the public: It’s up to you to hold Enbridge accountable – in everything they do. Don’t let them risk your lives by installing pipelines they now know to be compromised. Don’t let them risk lives by installing pipelines, period.
And lastly, but not least, to our comrades and co-conspirators:
A How-To from the heart
You’ll need 1 a decent cordless drill, 2 a good smaller-gauge cobalt or titanium drill bit – preferably with a pilot point, and 3cutting oil. [Oh, the irony!]
With a righteous sense of adventure, prove your stealth ninja skills by getting into the right-of-way. Once you’re in there you’re pretty invisible from the road so long as you’re not fluorescent, adorned in glitter of fucking around with a headlamp too much. Take a breath, take a look, and then find your way to an empty pipeline and start drilling! Go slow [so there’s less noise, reverberation, and friction] and apply enough pressure so that you see metal shavings coming up – and then keep at it for 10 to 15 minutes. Cutting oil will help the process along by keeping the drill tip cool and effective.
Have fun. Stay safe.
And get the fuck out there!